Component 1
1.4 Network security
Threats to computer systems and networks
Malware
Stands for malicious software – it includes any software that has been designed to cause harm to a user or the computer. Examples are:
- Virus: software that copies itself from machine to machine causing harm as it goes.
- Trojan horse: malware that is disguised as something beneficial e.g. a game or utility and only once downloaded does it cause damage.
- Spyware: malware that watches the keys you press trying to record your passwords and personal information.
- Ransomware: locks your computer and all the files so you can’t access it unless you pay the evil owner a huge sum of cash!

Social engineering
Sometimes, it is people that are the weak point in a system. Social engineering includes any number of techniques designed to trick people into giving away crucial data or passwords. Effectively this is the same as an old fashioned “con”. Some of the scams available include:
Phishing
A hacker sends out emails pretending to be from a trusted source. The emails will have a sense of urgency, asking the receiver to click a link and enter confidential information.
Shoulder surfing
The hacker simply tries to peer over your shoulder whilst you are typing in a password.
Vishing
Similar to phishing but this time a voice call is used to trick a victim into giving out their personal information.
Tailgaiting
If a hacker needs to enter a secure area, they can follow somebody who has access. Sometimes people are so polite, they will even hold the door open for the intruder.
Brute force attacks
One way to try to guess somebody’s password is to simply try every single possible combination of passwords available until the correct one is found.
Denial of service (DoS) attacks
A web server is flooded with requests so that it cannot cope with the demand and either shuts down or stops being able to answer the real requests.
DDoS (distributed denial of service attack) is a variant of this and involves the hacker taking over a whole host of computers and using them to perform the attack in unison. This makes it much harder to stop as the attacks are coming from different locations all around the world.
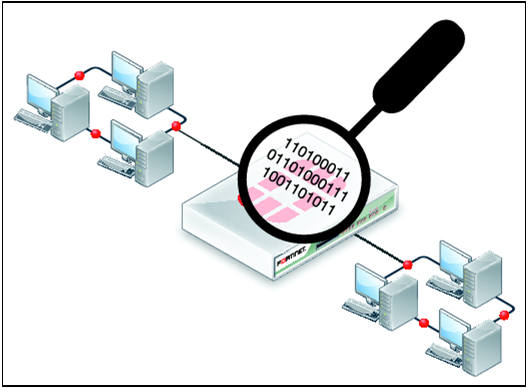
Data interception and theft
Each time any communication is sent across a network, whether it is a Local Area Network or a Wide Area Network, it is split up into packets and sent by various routes. As they travel from one part of the network to another, they are at risk of being intercepted, read, altered or deleted.
One way data can be intercepted is if someone uses some hijacking software and pretends to be the destination for communications across a network.
Another way is for a user to use 'packet sniffing' software and hardware to monitor network traffic and intercept those packets it is interested in. People using packet sniffers are especially looking for plain text files, passwords and set-up information being set across the network, which they can steal, analyse and extract information from.
The concept of SQL injection
Malicious code is entered into a form on a website that attempts to change the SQL statement that goes to the server.
This could mean that the criminal gets unauthorised access to data from the database or could delete / modify the data.
e.g. Adding ;DROP TABLE Customer to the end of a query string might delete a website’s customer data if it wasn’t securely protected.
Identifying and preventing vulnerabilities
Penetration testing
Sometimes called pen testing. This is when a company hires somebody with hacking skills to try to break into their system. If they are successful they can tell the company the weaknesses so that they can fix them and protect themselves from real attacks.

Anti-malware software
Protection software that stays in the computer’s memory. It is constantly scanning the drives and memory for any malicious software. It compares suspicious items with a known database of threats and reports it to you when there is a match. You can then choose to quarantine the file or delete it.
Firewalls
Scans incoming and outgoing traffic to and from a network. Compares traffic to a criteria to see if it should be allowed through and blocks anything that doesn't meet the rules. Can be used to block certain IP addresses or ports.

User access levels
Different users can be given different permissions (e.g. permission to read data, permission to write data, permission to delete data). Some data can be restricted to accounts that have higher levels of authority.
Passwords
Strong passwords can help to protect against brute force attacks. The longer the password the better and it helps if it contains numbers, a mix of capital and lowercase letters and special characters. Favourite football teams or pet names should be avoided as these will be in common password dictionaries.

Encryption
Uses a special algorithm to scramble up data.
It doesn't stop data being intercepted but means it can't be understood if it is. Only somebody with the correct key can unscramble it.
Physical security
Quite simply, its much harder to get access to data if there is a wall in the way or it is locked in a safe!
Physical security measures might include keypad entry to server rooms, biometric scanners to enter a room, guards and CCTV.
| Threat | How to defend |
|---|---|
| Malware | Use anti-malware software. Firewalls can block malware entering your network. |
| Social engineering | Good physical security measures. Train your staff to be alert. |
| Brute force attacks | Use strong passwords. |
| Denial of service | A firewall can block IP addresses that make too many requests. |
| Data interception | Encryption won't stop data interception but it will stop the data being understood. |
| SQL injection | Some firewalls can block SQL injection attacks. Good programmers know how to write code that blocks SQL injection as well. |