Component 1
1.3b Wired and wireless networks, protocols and layers
- Wired and wireless networks
- Encryption
- IP and MAC addressing
- Standards
- Protocols
- The concept of layers
Wired and wireless networks
Networks can be connected using wires or with wireless technology.
By far the most common wired technology is called Ethernet. It has become a standardised way to connect computers together and manufacturers around the world all make devices that can use it. You will probably have seen Ethernet cables yourself. Ethernet can support transmission speeds of up to 10Gbps (very fast). Ethernet cables do have a range limitation however and the signal starts to degrade after around 100m. This can be fixed by adding another switch before the effective range is reached.
There are two main wireless technologies:
- Wi-Fi: Wi-Fi is a wireless protocol that is designed to work alongside Ethernet. It uses radio waves to trasmit data, either at 2.4GHz or 5GHz. The latest Wi-Fi editions have a theoretical maximum speeds of 9.6Gbps but these speeds are often not achieved in reality. 2.4GHz Wi-Fi can reach around 45m indoors and 90m outdoors. 5GHz Wi-Fi is about one third of the range and can't penetrate walls as well but is often faster and less affected by interfering signals.
- Bluetooth: a short range wireless technology standard designed for communicating between two devices that are close together e.g. your phone and your headphones. The max range for consumer devices is about 10m and the max speed is just 2.1Mbps.

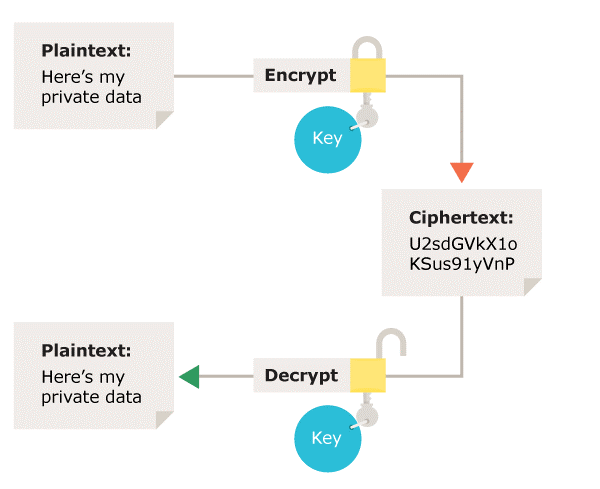
Encryption
The problem with sending data on a network is that a bad person could intercept the data packets and this could be a security risk if you were transmitting confidential information.
One way to combat this is to use encryption. Encryption will not stop data being intercepted. However, encryption scrambles data up so only the person with the correct encryption key can unscramble it. This means that when it is intercepted, the hacker can't read the data as it will just be an incomprehensible jumble to them as they won't have the key.
IP and MAC addressing
Each device that connects to a network is given an IP address by the router. An IP address is a unique number for that device and lets the router and switch send and receive data packets involving that device. IP addresses can change as needed - in your home network, for instance, your phone will reconnect to the network each time you get home and you may get a different IP address each time.
IP addresses have two formats. The first is called IPv4 and involves four numbers between 0 and 255, each separated by a full stop. Here is an example:
IPv6 is being introduced so that there will be more possible IP addresses. IPv6 uses 8 hexadecimal numbers which provides a huge amount of possible combinations. Here is an example:
Devices will also have a MAC address. This is a unique number that is hard coded into the hardware at the time of making by the manufacturer. Every device in the world has its own unique MAC address. MAC addresses are 12 hex characters long. Here is an example:
Standards
Many of the technolgies involed in computing are given standards. This means that leading experts in the world have agreed on a way to do something. The advantage of this is that everybody knows what to work towards and manufacturers can make devices that are compatible with each other. Common standards include:
- USB
- Ethernet
- Wi-Fi
- Qwerty keyboards
- HD resolution for monitors
- Coding, documentation and testing standards
- Communication standards (protocols - see below)
Protocols
A protocol is a set of rules used when transferring data across a network. You need to learn some of the more common protocols and what they are for.
| Protocol | What it stands for | What is does |
|---|---|---|
| TCP/IP | Transmission Control Protocol / Internet Protocol | For sending any data across the internet. |
| HTTP | Hypertext Transfer Protocol | For sending and receiving data about web pages. Has different methods such as GET and POST. |
| HTTP/S | Hypertest Transfer Protocol Secure | For sending and receiving encrypted data about web pages. |
| FTP | File Transfer Protocol | For sending files in a client server relationship. |
| POP | Post Office Protocol | For receiving emails. |
| IMAP | Instant Message Access Protocol | For receiving emails and syncing emails to the server. |
| SMTP | Simple Mail Transfer Protocol | For sending emails. |
| DNS | Domain Name System | Used for converting human readable domain names (e.g. learncomputing.org) into IP addresses and vice versa. |
The concept of layers
Protocols are often used together. When this is the case they are divided into separate layers. This is because:
- A layer can be changed or removed without affecting the other layers
- Each layer is self-contained and has its own purpose
- Each layer does not need to consider what the other layers do and can be programmed individually
- Individual protocols are smaller and simpler to manage
- Different layers can interface with different hardware
The OSI model lists all the possible layers. You don't need to know this for GCSE but it can be useful to look and see where the protocols and equipment fit.
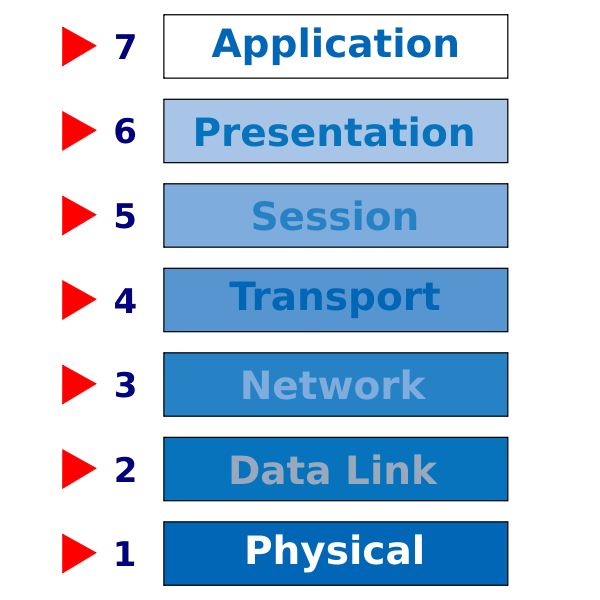
| Layer no. | Name | Equipment | Protocols / Standards |
|---|---|---|---|
| 7 | Application | Next-generation firewall, web-application firewall | HTTP, HTTP/S, FTP, POP, IMAP, SMTP, DNS |
| 6 | Presentation | encryption e.g. SSL; file formats e.g. jpeg, png; compression e.g. zip; text encoding e.g. Unicode | |
| 5 | Session | ||
| 4 | Transport | Firewall | TCP, UDP |
| 3 | Network | Router, firewall | IPv4, IPv6 |
| 2 | Data link | Switch, NIC, wireless access point | Ethernet (MAC addressing and frames), Wi-Fi (MAC addressing and frames), VLAN |
| 1 | Physical | Transmission media e.g. coaxial, ethernet cable; NIC; hub; repeater | Ethernet (physical properties), Wi-Fi (radio tranmission) |